|
Operation Log
|   |
Project settings and genealogy settings are defined by the Administrator for a project/organization level. These settings control all major operations in WRENCH Any change in the same would affect the normal working procedure. It may happen that a user may change these by mistake as well. Tracking such changes is crucial for trouble shooting issues that may raise due to such change in settings.
Operation Log will help the administrator to track/monitor any such changes done in the settings and trouble shoot by changing the settings.
To generate an operation log
Operation Log window is displayed.
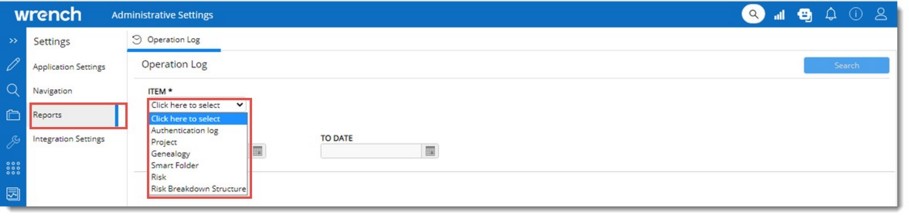
Figure: Generating a log of operations
This log provides information on different project operations.
To generate a log for project operations
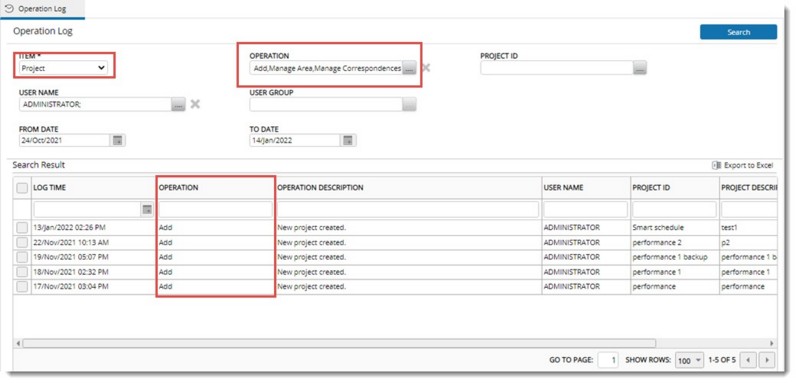
Figure: Operations log report for Project
This log provides details about genealogy operations carried out by a user or user group.
To generate report for genealogy operations
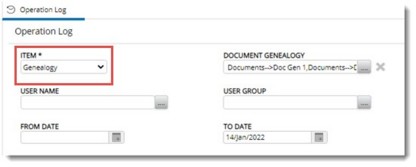
Figure: Operation Log for document genealogy
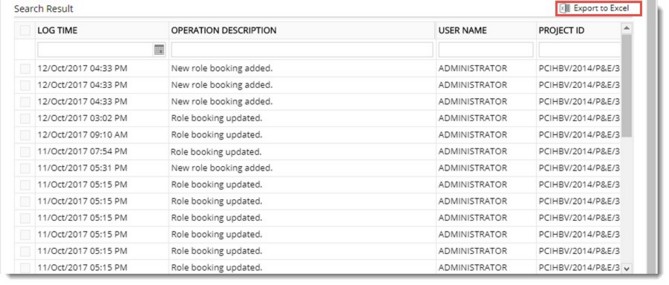
Figure: Search Results
This log provides information on different smart folder operations carried out by a user or user group.
To generate report for smart folder operations
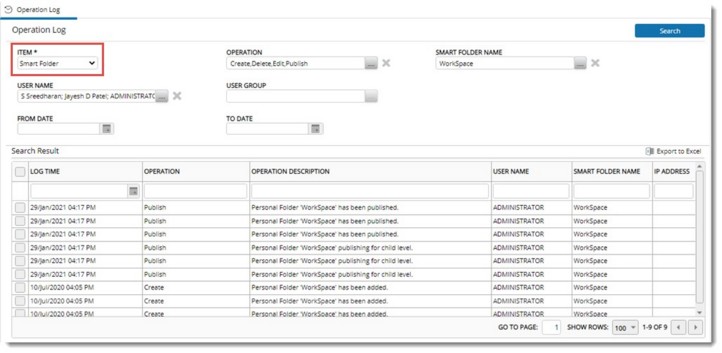
Figure: Operation Log for Smart folder
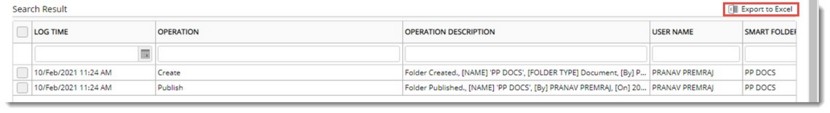
Figure: Search Results
This log provides information on different operations carried out on a risk by a user or user group.
To generate a log for Risk
NOTE: If Risk module is enabled for the user, in the drop-down list for selecting item, Risk and Risk Breakdown Structure will be available.
On selecting Risk from the drop-down list, the following window is displayed.
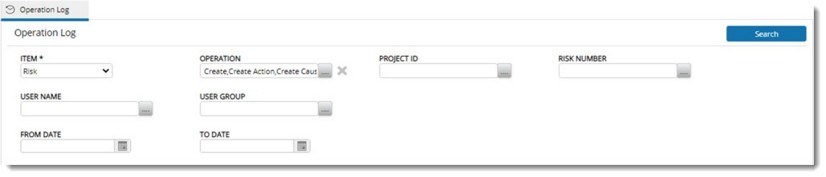
|
Property |
Description |
|
|
1 |
OPERATION |
Operation Details window is displayed. Here operations for which a log can be generated is displayed.
Figure: Operation Details window
|
|
2 |
PROJECT ID |
Project Search window is displayed.
|
|
3 |
RISK NUMBER |
Select Risk window is displayed. Created risks are displayed here.
Figure: Select Risk window
|
|
4 |
USER NAME |
Click the browse button to select single or multiple users from Search User window. The browse button will be disabled if a user group is selected. |
|
5 |
USER GROUP |
Click the browse button to select single or multiple groups from Groups selection window. The browse button will be disabled if a user is selected. |
|
6 |
FROM DATE |
Select the staring date for generating log. |
|
7 |
END DATE |
Select the end date for generating log. |
Selected values are displayed next to the fields.
Generated log is displayed in search results grid.
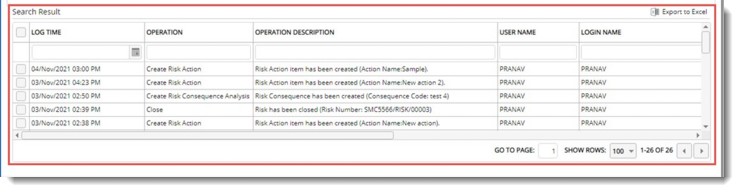
Figure: Generated log
For the operation Update, operation description is displayed as a hyperlink. On clicking the hyperlink, Update details window is displayed.
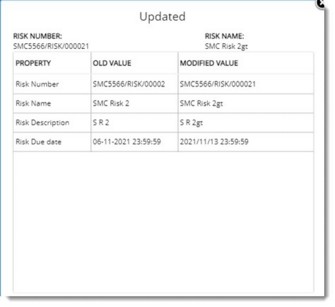
Figure: Update details window
Here the Old value and Modified value of properties are displayed.
If any columns are not selected in the excel sheet, entire contents of the sheet are exported. If specific columns are selected, only the selected columns are exported. A sample excel file is displayed in the following figure.
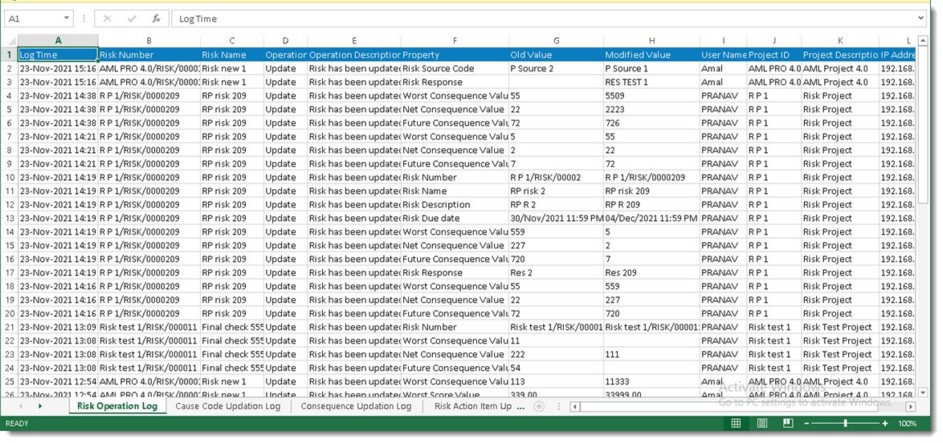
Figure: Exported log
Risk breakdown structure operations log
This log provides information on different operations carried out in the risk breakdown structure by a user or user group.
To generate a log for Risk Breakdown Structure
|
# |
Property |
Description |
|
1 |
OPERATION |
Operation Details window is displayed. Here operations for which a log can be generated is displayed.
Figure: Operation Details window
|
|
2 |
PROJECT ID |
Project Search window is displayed.
|
|
3 |
USER NAME |
Click the browse button to select single or multiple users from Search User window. The browse button will be disabled if a user group is selected. |
|
4 |
USER GROUP |
Click the browse button to select single or multiple groups from Groups selection window. The browse button will be disabled if a user is selected. |
|
5 |
FROM DATE |
Select the staring date for generating log. |
|
6 |
END DATE |
Select the end date for generating log. |
Generated log is displayed in search results grid.
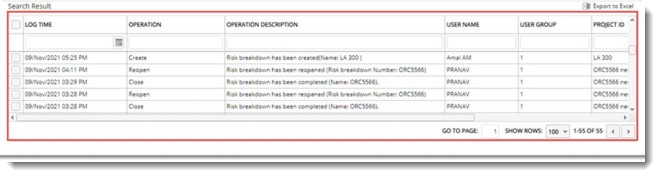
Figure: RBS log
If any columns are not selected in the excel sheet, entire contents of the sheet are exported. If specific columns are selected, only the selected columns are exported.
Viewing the list of log in attempts is required, when an audit is conducted in the organization.
To generate log for authentication
|
# |
Item |
Description |
|
1 |
FROM DATE |
Enter the date from which the operation log needs to be displayed. |
|
2 |
TO DATE |
Enter the date till which the operation log needs to be displayed. |
|
3 |
LOGIN NAME |
Enter the login name for which the operation log needs to be displayed. This is not mandatory. |
|
4 |
LOG CATEGORY |
Select the log category from a drop-down list. |
|
5 |
LOG TYPE |
Select the log type for which the operation log needs to be displayed from a drop-down list. |
A log is generated and displayed in the grid as shown in the following figure.
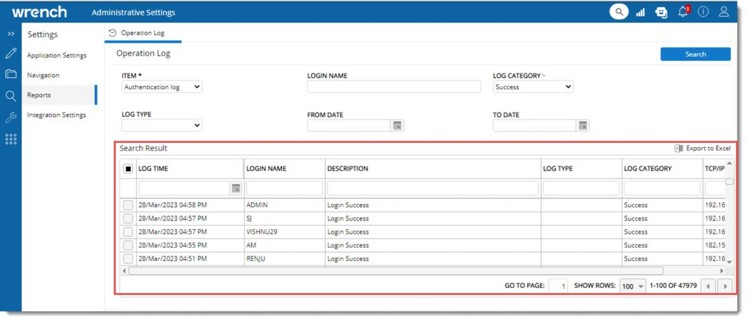
Figure: Authentication log
An administrator can view the details of the concurrent users logged in to the system.
To generate a concurrent login report
Figure: Generating a concurrent login report
The report is generated and in the report peak usage and unique usage for a date is displayed.
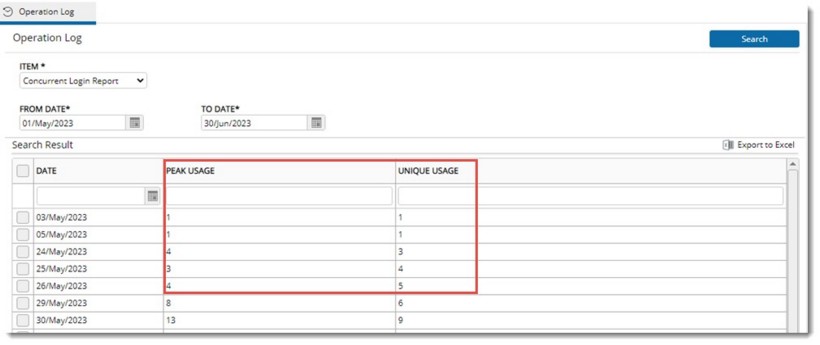
Figure: Concurrent Login Report
The values can be exported to an Ms Excel file.