|
Viewer Settings
|   |
For every client site, instead of configuring individual Rasterex instance, multiple clients can access a single instance. A central server is configured for a region and the clients belonging to that region will access Rasterex from that region’s central server.
To configure viewer settings
Settings can be defined for Autodesk Forge Viewer and Rasterex Viewer.
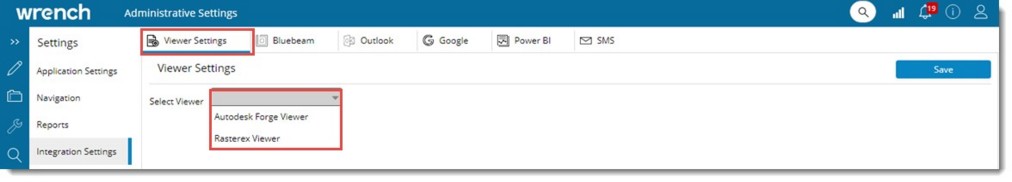
Figure: Viewer Settings
If the viewer type selected is Rasterex Viewer, the following window is displayed.
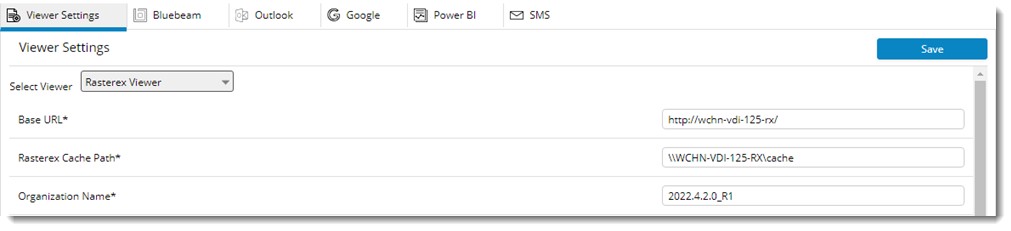
Figure: Defining setting for Rasterex Viewer
|
# |
Property Name |
Details |
|
1. |
Base URL |
Enter the Base URL Path. |
|
2. |
Rasterex Cache Path |
Enter the Rasterex Cache Path. |
|
3. |
Organization Name |
Enter the organization name which has been provided at the time of purchasing the Rasterex license. |
|
4. |
Data Retention Policy |
Specify the number of days in which the cache files has to be stored on the server. |
If the viewer type selected is Autodesk Forge Viewer, the following window is displayed.
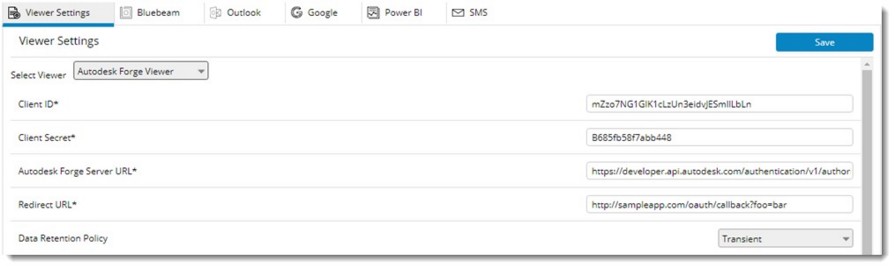
Figure: Defining setting for Autodesk Forge Viewer
|
# |
Property Name |
Details |
|
1. |
Client ID |
Specify the client ID. |
|
2. |
Client Secret |
Specify the Client's Secret details. |
|
3. |
Autodesk Forge Server URL |
Specify the Autodesk Forge Server URL. |
|
4. |
Redirect URL |
Specify the Redirect URL. |
|
5. |
Data Retention Policy |
Select the data retention period as per the company policy from a drop-down list. The options available in the dropdown list are as follows:
|
When a file is opened in the viewer, the system checks whether the user has the security permissions to view this file. If the user has the permissions, then the system shall check whether the selected file is available in the respective viewer's folder. If the file is available in the folder, then the file is opened in the viewer
If the file is not available in the respective viewer folder, then the file is downloaded from the vault and is displayed in the configured viewer.
NOTE: Currently the files are copied from the vault each time a user attempts to view the file. Instead of this, a cache is maintained, where these files can persevere. Security rights of the user are evaluated before granting access to the file.