|
Configuring Authentication for Vendors
|   |
In a typical work day user may use multiple websites and applications to get their work done. This means that they may have to remember multiple login credentials which may be difficult for them. To tackle this issue single sign-on facility can be specifically configured for Vendors.
To configure authentication
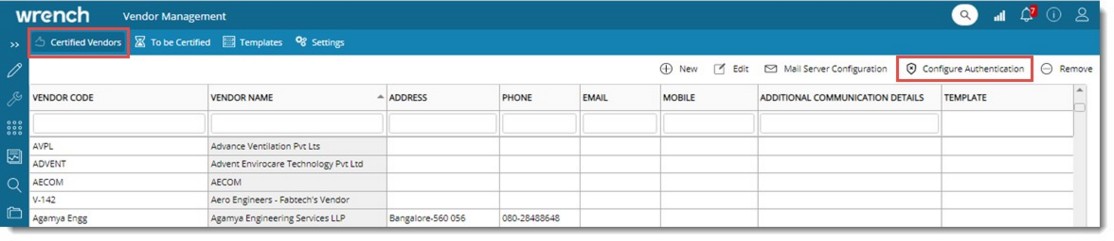
Figure: Vendor Management window
Configure Authentication window is displayed.
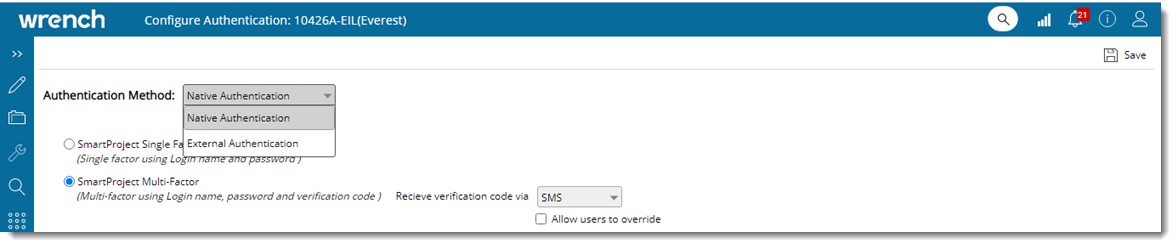
Figure: Configure Authentication window
SmartProject supports both Native Authentication and External Authentication. In the case of Native Authentication, option to authenticate using single factor and multi factor is available. In the case of External Authentication, option to authenticate using MS Office and OKTA is available.
 To configure native authentication
To configure native authentication
Configuring External Authentication
Option to login to SmartProject using Office 365 or OKTA credentials and Active Directory Services credentials will be available.
A integration between SmartProject and Office 365 or Okta can be defined here.
To configure external authentication
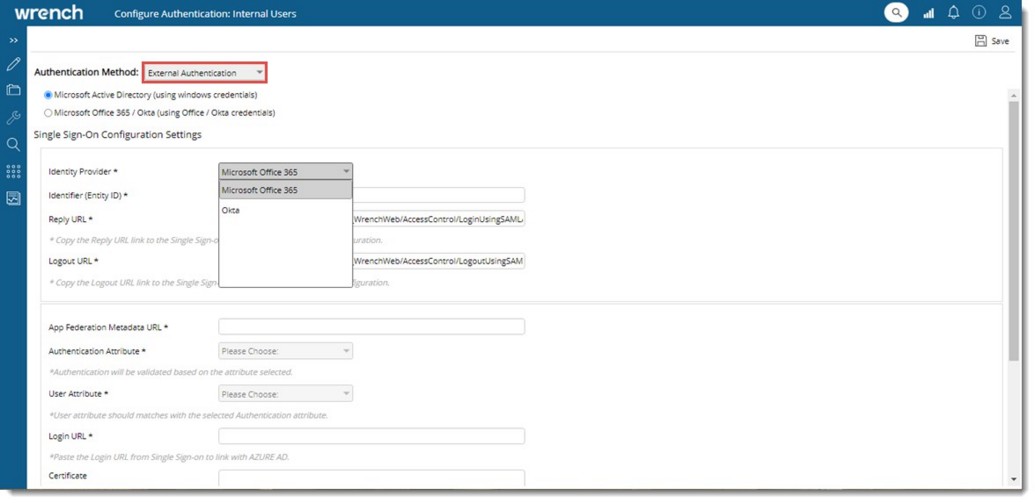
Figure: Configuring Single Sign On
Single Sign On Configuration Settings window is displayed. Configuration can be defined for Microsoft Active Directory and Microsoft Office/Okta.
Identify Provider: Select an Identity Provider from a drop-down list. Options available in the drop-down list are Microsoft Office 365 and Okta.
By default option Microsoft Office 365 is selected. If there are any saved configuration it is displayed in the window.
NOTE: When the Identity Provider is changed from the drop-down list, a warning message Do you wish to clear the existing configuration is displayed. On clicking Yes, existing configuration of the currently selected identity provider is removed, and the fields are cleared. On clicking No, existing configuration values are not cleared.
Identifier (Entity ID): This URL is unique and identifies the application. Copy-paste the same URL from Active Directory. Login URL from AD only contains the base URL path. Append the encrypted request using the reply URL and Identifier (Entity ID) while login.
Reply URL: This url specifies where the application expects to receive the SAML token. The reply URL is also referred to as the Assertion Consumer Service (ACS) URL.
Logout URL: This URL is used to send the Single Sign On Logout responses back to the application. This is mandatory if the selected identity provider is Microsoft Office 365. For Okta this URL is not mandatory.
App Federation MetaData URL: Specify this URL to allow user to access the metadata specific to the application.
Authentication Attribute: Specify the authentication attribute, which helps SmartProject to validate the user. Options Email ID and Login Name is available in the drop-down list. By default, Email Address is selected.
User Attribute: Specify the field name corresponding to the Authentication Attribute in the Federation MetaData XML retrieved using ‘App Federation MetaData URL. Once user pastes the metadata URL, corresponding attributes in the XML file will be listed in User Attribute drop down. User should select the right attribute relative to the authentication attribute.
Login URL: Specify the login URL. When a user opens this URL, the service provider redirects to Azure AD to authenticate and sign on the user. Azure AD uses the URL to start the application from Microsoft 365 or Azure AD My Apps.
Certificate: Enter the trust key to decrypt the response from Identity provider.
Configuring Okta SAML Settings
To enable Okta single sign on configuration, user has to configure SAML setting in Okta administration page.
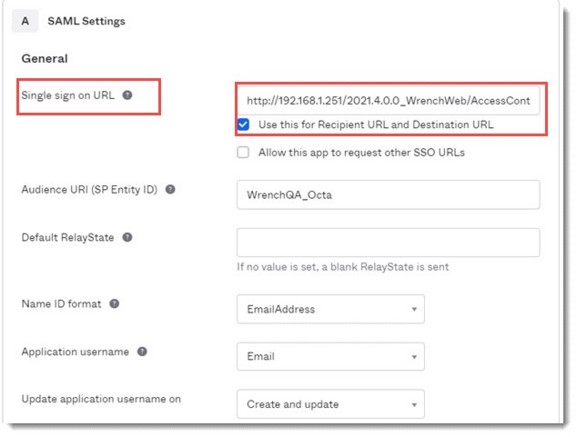
Figure: Configuring Okta SAML Settings
To Integrate SSO
If the authentication mode is configured for Okta sign on, user will be redirected to Sign on URL which will be the login page of Okta. Once successfully logged in with Okta, user will be redirected to the ‘Reply URL’ defined, where the ‘email address’ or the ‘Login Name’ (as configured) will be available. SmartProject will use this Okta login credentials to identify the corresponding SmartProject user account.